Support us and whitelist the internet site with an advertisement-blocking plugin. Integrations support us to consistently build the venture
Practically all of these kinds of computer software deploy by themselves and use process vulnerabilities to contaminate other equipment, capture unique data, or just disrupt or hurt a tool.
a hundred entities monitored consistently over the prolonged organization Usage of constructed-in aid means and leading-exercise elements
Compliance and legal: Consist of clauses in third-get together contracts that handle compliance, legal responsibility, and chance mitigation and make sure all distributors are offboarded safely and securely soon after agreement expiration.
In response for the Dridex assaults, the U.K.’s National Cyber Safety Centre advises the public to “guarantee units are patched, anti-virus is turned on and updated and documents are backed up”.
Down load our toolkit to construct a compliant and thorough 3rd party chance administration plan. Our toolkit simplifies the language inside the ISO 27036 conventional so that you can Make your TPRM program with self-assurance.
使用硬件和软件来监控、检测和控制工业系统变更,全方位保护关键基础设施。
It doesn't matter how sturdy these assurance expectations are, interorganizational dependencies are special, and uniquely granular, to a degree exactly where the CyberSecurity answer calls for custom-made due diligence. A contractual shared Alternative across all vendors will not be sufficient, for “very little in business enterprise functions continues to be in a gradual state….”9 A drive majeure
An organization’s TPRM software can only be certainly successful when all departments and staff members undertake avoidance procedures and abide by finest practices.
Functions: Identify and mitigate offer chain hazards and be certain continuity for the duration of a third-bash disruption.
Inadequate safety measures could expose your equipment and facts to unsafe threats like destructive computer software.
Real-time chance insights: Spreadsheets can’t tell you what transformed yesterday, but Isora can. It continuously tracks your seller ecosystem and helps your Firm track pitfalls in a central risk sign-up — all easily available and at a look.
Cloud providers think a shared safety product, in which cloud vendors are liable for the infrastructure and shoppers are to blame for securing the programs jogging to the infrastructure.
Furthermore, our scoring algorithm makes use of a statistical framework that can take into consideration the a lot of rated corporations over the SecurityScorecard platform.
 Dylan and Cole Sprouse Then & Now!
Dylan and Cole Sprouse Then & Now! Kenan Thompson Then & Now!
Kenan Thompson Then & Now!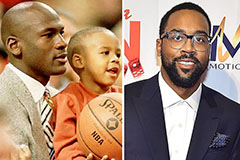 Marcus Jordan Then & Now!
Marcus Jordan Then & Now! Nadia Bjorlin Then & Now!
Nadia Bjorlin Then & Now! Robin McGraw Then & Now!
Robin McGraw Then & Now!